These Are the Best VPNs for Travel Right Now
We may earn a commission from purchases you make after clicking links on this site. Learn more.You’ve probably heard it already (I certainly go on about it enough): a VPN is one of the best investments you can make in your online security.
This is true at any time, but especially when you travel. From dodgy public Wi-Fi to blocked websites, government surveillance to locked bank accounts, a good VPN makes your travels safer and easier for just a few bucks a month.
That’s not the only reason to use a VPN, however; in fact, for many people, it’s not even the most important. With the right service, you’ll be able to keep watching your favorite streaming shows from back home, even when they’re usually unavailable in whatever country you’re in.
The whole thing can be a bit confusing, though, which is why I decided to try and demystify it all. Below, I explain what a VPN actually is, and why you’d want to use one when you’re on the road. I also cover exactly what they are (and aren’t) good for, which one I personally use, and a few worthwhile alternatives.
Let’s get started!
Just want the recommendations?
So What Is a VPN Exactly?
A VPN (virtual private network) is like your own secure, private tunnel to the internet. All the information you send and receive online is scrambled and encrypted before it flies through the air and over the wires, keeping it safe from prying eyes.
In practical terms, this means that all your activity (the sites you use, login information, your online messages and calls, everything) is kept private. With the possible exception of the VPN company itself, nobody will know what you do online or have access to anything you type or view.

Why Travelers Need a VPN
Bypass Censorship and Blocked Sites
Depending on where you’re traveling to, you may find the internet to not be the unrestricted free-for-all you’re used to. Many popular online services are blocked in certain countries, including several you probably take for granted in daily life.
Google, Facebook, Twitter, WhatsApp, Skype, and others are simply unavailable in some places due to local laws. You’ve probably heard of the Great Firewall of China (if you haven’t, here’s a handy primer), but while it probably has the most effective blocks, China isn’t the only country with restrictions.
Other Asian nations have them as well, as do several Middle East and Gulf countries, Australia, the United Kingdom, and many others.
A VPN can help you access blocked sites by routing your connection via a server in a different country. Most VPN companies have servers around the world, so your visit bypasses the filter in whatever country you’re in and appears to come from (eg) Canada or Estonia instead.
This also works for websites that work differently (or not at all) based on where you’re accessing them from. If a site you want to visit is only accessible from a specific country, you can set your VPN to a server within that country, and voilà, you’re in.
Equally, if a multilingual site detects your location and insists on showing content in the local language, try using a VPN to make it appear like you’re browsing from somewhere else in the world.
Avoid Being Locked Out of Your Bank Account
Have you ever tried using your credit or debit card abroad, only to have it declined and your account locked for unusual activity? Yes, me too. It never stops being annoying. Telling your bank in advance that you’ll be traveling helps with this, but trust me, it’s not foolproof.
Granted, this security is at least somewhat for our protection. If my card is ever stolen, I’ll be happy if my bank flags weird purchases right off the bat. But if it’s just me booking a hotel in Budapest while I’m in Prague, I really don’t want to spend the next half-hour on hold with the fraud department. Enter my VPN.
Your bank knows where the transaction is taking place based on the IP address. So, if you set your VPN to make it seem like you’re logging in from your home country (or even better, home city) instead of Prague, it’ll raise fewer red flags. There’s less risk of your account being frozen, or having to jump through extra security hoops.
This applies to other financial services as well. PayPal is notorious for freezing your account because you’re logging in from a different country, and getting it unblocked can take forever. A VPN is a simple solution that can save you a lot of phone calls, messages, and wasted time.
Secure Your Online Activity
Public Wi-Fi can be a lifeline when traveling. Even if you buy local SIM cards or eSIMs, or have affordable roaming, you’re bound to rely on shared Wi-Fi at some point.
Insecure connections like these come with a big drawback, though: they can expose your data and online activity to anyone else on the network who knows how to look for it.
The rise of secure (HTTPS) websites has helped reduce this risk, but there are still plenty of insecure sites, apps, and services out there. Fire up a VPN on your device, however, and you’re protected from snoops on even the dodgiest of airport networks.
Because VPNs encrypt all your data before it gets sent over the Wi-Fi, it just appears as incomprehensible garbage to anybody trying to see what you’re up to.
Protect All Your Devices
In the past, VPNs were typically associated with corporate workers connecting back to head office from their laptops. That’s definitely not the case now, especially for leisure travelers who often aren’t carrying a laptop at all.
As we’ve started to use our smartphones and tablets for, well, everything, the need to protect our data and online activity on them has increased dramatically.
Most good VPN services offer dedicated iOS and Android apps, including all the companies I recommend below. They won’t protect you if you don’t use them, though.
Make sure the app is installed on each device you’re traveling with, and set it to connect automatically. Most VPN subscriptions allow several simultaneous connections from a single account, so there’s really no reason not to.
Do VPNs Have Any Drawbacks?
VPNs do a good job of protecting your data and making your travels easier, but they’re not a magic bullet. As they’ve become cheaper, simpler, and more popular, repressive governments and profit-hungry media companies have started paying attention to them.
They Don’t Work in Every Country
While VPNs can help get around internet censorship, they’re not a global panacea. Some countries have banned the use of VPNs, or require them to be registered with the government (meaning most travelers wouldn’t be allowed to use them). Examples include Belarus, Russia, Iraq, Iran, Turkey, Uganda, and Oman.
This doesn’t mean that standard VPNs don’t work at all. In many of the above countries, their use is actually quite common among citizens. It does mean, however, that you could get in trouble if you’re found using one while you’re inside the country.
Several Middle East countries, including Qatar and Bahrain, allow VPNs on their networks but block access to the VPN providers’ websites. As long as you download and install the software before reaching these countries, they should work just fine.
Some countries, like Venezuela, have tried blocking VPNs. Most haven’t succeeded at this point, but China is a special case. The country has been somewhat successful at blocking VPN usage in the past, but these blocks usually go in cycles.
During times of civil unrest, important government meetings, or country celebrations, VPNs often stop working well or at all in China. They’ll typically return to normal after a few days or weeks.
Frequent travelers and expats in China are very familiar with the situation, as it’s been the case for several years. Some of the VPN providers listed below specifically cater to China, so be sure to pick one of them if the Asian giant is in your travel plans.
They Usually Cause Slower Connections
The one big drawback of all VPNs: they’ll usually make your connection more sluggish. While there are a few cases where they’ll improve the situation, those are rare. The rest of the time, expect slower speeds.
There’s really no way around it, but the degree to which things slow down depends on the VPN service you use, the location of the server you’re connected to, and the speed of the internet connection wherever you physically are.
Changing servers to one that’s geographically closer can help, as can switching the VPN protocol. The exact method for doing this varies by app, but is typically straightforward.
Many Are Blocked by Streaming Services
Once upon a time, VPNs were a great way of getting country-specific content from streaming services. If you wanted to access US Netflix or BBC iPlayer, you just used your VPN to connect to a server in the right country and away you went.
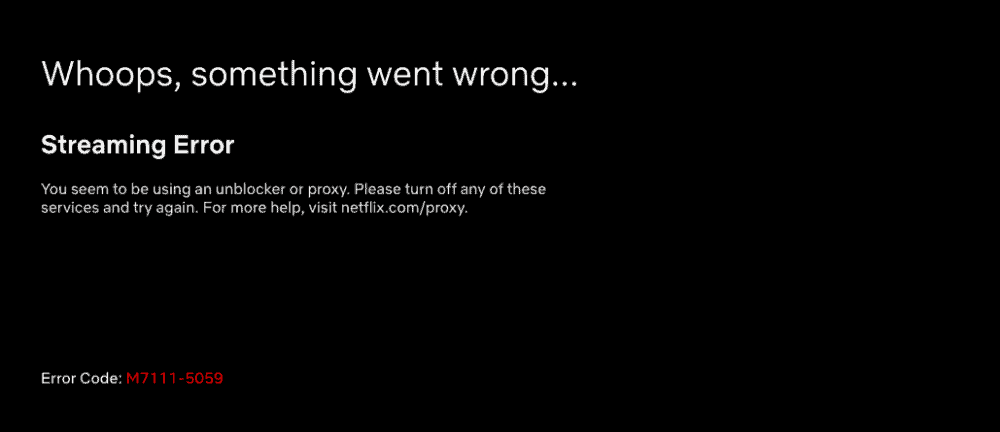
It’s often a different story these days, unfortunately. Netflix now detects the vast majority of commercial VPN services, for instance, especially the free and cheap ones. If you’ve got one of these running, you’ll just get an error message, accompanied by error code m7111-5059. You’ll have similar problems with Hulu, BBC’s iPlayer, and others.
With Netflix, at least you can still access whatever content is available locally, since it operates in 190+ countries. With others that only offer service in one or two countries, you’ll be out of luck anywhere else.
Fortunately, a (very) small number of VPNs do manage to bypass this block by using special servers, however, including the one I use: ProtonVPN. It’s an endless game of cat and mouse as streaming services block each server one by one, but with the right VPN, it’s still possible.
Other services do run with VPNs on, such as YouTube Premium. Keep in mind, however, that the video will be slowed down significantly. You’ll need a faster connection than usual to have any chance of a smooth viewing experience.
We talk a lot more about using VPNs with Netflix, Amazon Prime, and other streaming services in this article.

Which VPN Is Best for Travel?
Now, the big question: which VPN service should you choose as a traveler?
I’ve used many of them over the years, and while there’s one that stands out above the rest, several others also score consistently highly, both with me and other travelers. These are my current picks for speed, features, price, and ease of use.
Best Overall: ProtonVPN
After putting ProtonVPN through its paces for several months on the road, I’m happy to recommend it as the best VPN for travel. Why? I wrote a detailed review of my experience, but in short: it was fast, reliable, and let me stream my favorite shows while avoiding censorship and government surveillance everywhere I went.
I’ve used many other VPN services over the years, including all of those mentioned below, but ProtonVPN outperformed them all where it mattered. It’s developed and run by a company that’s more transparent and trustworthy than most in this space, and there’s no logging, with the independent security audits to prove it.
It barely slowed down my internet speeds, and despite being continually enabled on both phone and laptop for months, I didn’t notice a single dropped connection. I was always able to watch shows on Netflix and BBC iPlayer without errors or buffering, and it supports many other streaming services as well.
This level of streaming performance is something I’ve never experienced with other VPNs in the past. If watching your favorite shows is important to you when you travel, ProtonVPN would be my pick above anything else.
With 4650+ servers in 90+ countries, a wide range of supported platforms including Linux, gaming consoles, and more, and high-security options like Secure Core and Tor support, it’s clearly a premium product, and that’s reflected in the price as well.
While there’s a basic free tier to get you started, the Plus version is what you’ll need to use streaming services while overseas. You’re allowed ten simultaneous connections with this plan, and will pay $4.50-10/month depending on how long you sign up for.
It’s not the cheapest option out there, but for me, it’s been more than worth the money. I renewed my subscription when it ran out, and will do so again in the future.
Runner-Up: ExpressVPN
Before switching to ProtonVPN, I used ExpressVPN for several years. With servers spread across 100+ countries, high speeds, and nearly two dozen supported platforms that you can run it on, it’s a pretty compelling option.
It’s been one of the best VPNs for travel in China in recent years, often continuing to work when others are struggling. While there are never any guarantees when the government does one of its crackdowns, the company continually monitors the network and has worked around most blocks in the past.
There’s 24/7 chat and email support if you’ve having problems, and no logging of your connection or activity data. The app is straightforward to install and use, with minimal configuration needed to get up and running.
One feature I particularly like is being able to run a speed test across the entire ExpressVPN network. This means it’s easy to find the server with the best performance wherever you are right now.
This level of service and support comes at a price, of course. ExpressVPN is more expensive than many of its competitors, especially if you pay month-by-month. That cost roughly halves if you sign up for a year, though, to around $7/month. You’re allowed up to eight simultaneous connections per account.
It takes the runner-up place for me mostly due to price: unless you get it on a particularly good sale, it’s more expensive than ProtonVPN for a similar level of service. That’s what caused me to switch in the first place, and I’ve been more than happy enough with Proton that I haven’t wanted to change back.
If you happen to be buying when there’s a sale on, though, you won’t be disappointed by ExpressVPN. Basically, just get whichever of these two options is cheapest on the day!
Budget Pick: VyprVPN
If both Proton and ExpressVPN are too expensive for you, and you looking for a cheaper option that still has good performance, check out VyprVPN. I used to use it several years ago, and while I ultimately moved on to other services, I’d be more than happy to switch back if I had to.
While it doesn’t have quite the same global reach (700 servers, 70+ countries) as some of the others, it owns all of its own infrastructure, giving it the edge in performance and security over some of the other lower-cost providers that just rent server space.
The app interface is straightforward and easy to use, with support for all the usual suspects (MacOS, Windows, iOS, Android, and more.) There’s 24/7 support, and the service has been audited to back up its “no logging” claims.
VyprVPN is another top performer in China, using a variety of approaches to ensure the service stays available over time. The company has been quick to respond to new or more aggressive blocking techniques over the years.
Pricing depends on how long you sign up for and whether any sales are running, but it can be extremely competitive. I’ve seen long-term subscriptions as low as $2.50/month at times, but even at standard pricing, it’s only $60/year ($5/month). You’ll pay double that if you sign up by the month, though.
The company simplified its plans recently, so all new subscriptions now include five simultaneous connections and the proprietary “Chameleon” technology that helps work around attempted VPN blocking.
Alternative Budget Pick: NordVPN
If you’ve ever watched a YouTube video from anyone in the travel space, there’s a better-than-average chance they were sponsored by NordVPN. The company seems to spend a lot of its marketing budget there, at least based on the videos I watch!
This site definitely is not sponsored by NordVPN or anyone else, but I still used the company’s service for a while. There are a remarkable number of servers on offer, nearly 6000 of them in total, but the geographic spread isn’t as high as some of the others: those servers are only in 60 countries.
Speeds were generally good in my testing, and when they weren’t, swapping servers typically solved the problem. I found both Proton and ExpressVPN to be reliably faster, but there’s not always a lot in it.
Security features are good for a lower-cost VPN like this. As well as a strict no-logging policy, you’ll get things like “Double VPN,” where your data travels via two different VPN servers, and “Onion over VPN,” where your connection goes over the Tor network.
Pricing is good with Nord, at least when you sign up long-term. While the month-by-month price is unexciting at around $13, that drops to a bargain $2.99/month if you pay for two years upfront. You’ll get up to six simultaneous connections, slightly better than most of the budget competition.
Performance is typically good in countries with serious censorship like China and Saudi Arabia, although NordVPN has had a few problems in China in the past. The company does maintain a special list of servers for use in heavily-restricted countries, at least, accessible from within the app.
Get regular updates from the world of travel tech and remote work
News, reviews, recommendations and more, from here and around the web
Free Trial: TunnelBear
Want to dip your toes in the VPN waters before you commit? Go with TunnelBear, one of the few good VPNs out there with a useful free offering. You’ll get 2GB of data per month to test the service out at no cost, with no other restrictions. If you’re not streaming or using it a lot, that might be all you need.
While it doesn’t have the same global reach as some of the competition, Tunnelbear still maintains 5000+ servers in around 47 countries. The app (available for the main desktop and mobile platforms) is cute and very easy to use, and you can get set up with just a few clicks or taps.
The company has a strong privacy focus, with a no-log policy and regular independent audits. Clearly aimed at those just getting started with a VPN, the focus here is on simplicity rather than high-end features. As a result, don’t necessarily expect it to work well in China or for streaming services.
Once you’ve used up your free allowance, you’ll pay $9.99 for a single month, or as little as $3.33/month if you sign up for longer. Paid options let you connect an unlimited number of devices, choose a specific city rather than just a country to connect through, and more.
In my testing, I found that speeds varied quite a bit, between “ok” and “very good”. If one server was particularly slow, switching to a different one usually improved the situation.
In short, Tunnelbear is a good, cheap option that’s reliable and easy to use, with a more-than-useful free tier. Sometimes, that’s all you need!
Not sure which one to choose? Go with ProtonVPN. It costs a bit more than the budget options, but has the best mix of speed, reliability, and security I’ve come across, plus the ability to consistently stream your favorite shows no matter where you happen to be.
It works on any device you’re likely to be traveling with, has top-notch support, and is developed and run by a company that’s a lot more trustworthy than most in this space.
While choosing the right VPN for your needs is important, the most important thing is that you use one at all. Your travels will get easier, your data will be safer, and you’ll be able to keep accessing your favorite sites no matter where in the world you are.
If that security and peace of mind isn’t worth a few bucks a month, what is?
Images via Anne Worner (feature image), Doctor Rose (broken key), Christiaan Colen (coding), Book Catalog (smartphone),








Hey mate,
So do you get a performance hit (or at least one that is perceivable) from a VPN?
What about uploading and downloading files to websites etc?
Cheers,
Colin
Hey Colin,
Depends. Sometimes I get *better* connections with Skype, as well as other times I’m being throttled.
I rarely notice a major performance hit, though there has got to be even a little one regardless as you’re adding another point of connection. Nothing noticeable day to day, but I suppose that depends on how fast your connection is to begin with. If you had a very fast connection, I’m sure you would be more apt to notice.
Great post. Guess I’m investing at least $5.99 for my month in Burma! Now if only a vpn could make the actual connection a bit faster…
In some cases, where bandwidth is throttled based on the kind of data sent (such as P2P), a VPN can make your transfer speeds faster!
This is so helpful, thanks, Dustin! I’ve managed to scrape by without getting locked out of PayPal or my bank accounts while in the U.S. and Argentina, where I spend a lot of time, but it sounds like something I need to be careful about. And the added security for open Wi-Fi connections is also appealing.
Awesome, thanks! Just came back to this article so I can link to it an my upcoming program. And I’ll be mentioning your site in general as a great resource on travel and technology.
I’ve tried from New Zealand – for Hulu – and even though I have reasonable broadband VPN makes it far too slow to stream video. Burma was at dial-up speeds so I’m even more curious to know if you have actually used a VPN in any of these countries and if so what speeds you got
Hey Lissie,
To be fair, New Zealand internet isn’t great. It was horrible 3 years ago when I was there last, and I’ve already made arrangements for an internet backup plan when I’m back there next month!
Technically, by the nature of having a middleman on your internet connection, you can never be faster than your slowest part. What I mean is that if your internet connection itself is slow, realistically connecting to a VPN shouldn’t be any faster. That said, if your internet provider (or country) shapes packets (VOIP, torrent etc), a VPN could make your connection faster for those purposes.
I’ve used a VPN in over 20 countries now, and for 3 months in Burma this past year alone. Of course, it really depends on your connection, but connecting to the VPN should use very little data (less than 100kb) so after connecting there shouldn’t be much issue.
Lastly, the quality of your VPN provider, and where you connect to will certainly play a role in how well a VPN works for you. I hear from many people who have used a free VPN-like service and remarked how horrible their experience was. Of course, your mileage will vary depending on more than a few factors. Think of it like an art rather than a science.
Hope that helps, Thanks for the comment.
Great info! I’ve been able to use a couple of the free ones occasionally, but Amazon has some stuff for Prime members I’d really like to be able to access when we have good bandwidth, but their system is smart enough to know it’s been tricked and blocks it.
I’ve had this problem with some sites too! So far I’ve only used free VPNs (mostly Hotspot Shield), so I wonder if the paid ones don’t have this problem? Would love to hear others’ experience with that.
Just considering the security aspect only, is there any advantage to using a VPN when accessing a HTTPS web site? Most of the sites that I care about security with (banking or purchasing) are HPPS.
Good (and geeky) question Chris.
While a website using HTTPS (and there are a lot more than there were a couple of years ago) is good, it’s still not 100%.
First, there are still many sites that don’t use HTTPS (as you mentioned).
Second, some sites use HTTPS for the main login, but not afterward. This is something that sites sometimes do to lower overhead on their servers, but it can potentially put your information at risk.
So given those two things, I would definitely still recommend using a VPN. It just takes one bad bit of code to put you at risk, and that’s too much to leave to chance.
Can I be a numbskull and ask for clarification of a few things?
We’re off to Vietnam soon and as such access to Social Media (Facebook), communication apps (WhatsApp) and bank privacy (checking online accounts) are all pertinent issues! I also aim to use NetFlix if I can ever find good enough WiFi access!
Will a VPN like Hola cover stuff like this or do I need something a little more ‘professional’ sounding such as the VPNs mentioned here?
I definitely wouldn’t be using Hola when accessing anything to do with your finances — they’ve been doing some pretty shady stuff recently.
While technically a proxy service (like Hola and others) will let you do all the things you’re talking about, there’s no real reason to use one over a VPN — especially since you can get free VPN accounts with services like Tunnelbear that may well do everything you need while you’re away. If not, they cost very little for the full-service accounts.
Thanks for getting back so quickly!
So, to paraphrase!!
If I use something like TunnelBear, it is more security-safe than Hola.
And, if I use TunnelBear, I will be able to use sites like USA NetFlix in Vietnam, use FaceBook and also check my bank account whilst over in Vietnam too.
I don’t mind paying a fee as, I’m only there for the month; in your opinion which is better (safer and easier to use), TunnelBear or Witopia?
Thanks again!
Yup, Tunnelbear etc is safer than Hola, and you’ll be able to access anything you can at home (assuming you’ve got a decent Internet connection, of course).
Tunnelbear is probably easier to set up, and they’re both easy to use.
Is it possible for a airbnb host to block using a VPN on their wifi? I had NordVPN on my laptop on a recent trip to Italy, on more than one occasion staying at different airbnbs when I would log onto the wifi as soon as I turned on the VPN I would not have internet service, could reach no websites. I tried different servers and every trick I could come up with but the only thing that worked was disconnecting the VPN and then it was fine. Any ideas?
Have you tried Proton VPN at all? If yes what are your views on it? These guys seem to be doing quite a good job at giving access to Netflix. Plus they are based in Switzerland and don’t keep any logs, for those for whom privacy is very important.
I haven’t tried Proton VPN as yet, so don’t have any real views on it. Beyond the limited free account, pricing is on the high side compared to some of the other contenders, but not hugely so. I know ProtonMail has a good reputation among privacy-conscious folks, so you can probably believe their no-logging claims.